I. Understanding Data Breaches
A. What is a data breach?
A data breach refers to a security incident where unauthorized individuals gain access to sensitive and confidential information. This can occur in various forms, such as when hackers infiltrate a company’s network, an employee accidentally exposes data, or physical documents are lost or stolen. Essentially, any unauthorized access, acquisition, or disclosure of protected information constitutes a data breach.
B. Types of data breaches
Data breaches can take many shapes and forms. Some common types include cyberattacks, phishing scams, malware infections, insider threats, physical theft, and third-party breaches. Each type presents unique risks and challenges, requiring tailored responses to effectively mitigate the impact.
C. Impact of data breaches
Data breaches can have dire consequences for individuals and organizations alike. For individuals, the exposure of personal information can result in identity theft, financial loss, reputational damage, and emotional distress. On the organizational front, data breaches can lead to financial repercussions, regulatory penalties, litigation costs, brand damage, and loss of customer trust.
Understanding the various aspects of data breaches is crucial in order to develop an effective data breach response plan. By recognizing what constitutes a breach, the types of breaches that can occur, and the potential impacts, you can better prepare for such incidents and mitigate their consequences.
Importance of Having a Data Breach Response Plan
Having an effective data breach response plan is crucial in today’s digital landscape, where data breaches have become all too common. This section will delve into the reasons why having a data breach response plan is necessary and the benefits of implementing such a plan.
Why is a data breach response plan necessary?
A data breach can have severe consequences for businesses, including financial loss, reputational damage, and legal ramifications. A well-defined response plan allows you to act swiftly and effectively when a breach occurs, minimizing potential harm. It provides a clear roadmap for handling the incident, ensuring that all key stakeholders are aware of their roles and responsibilities.
Benefits of an effective response plan
Developing an effective data breach response plan brings several advantages. Firstly, it enables you to respond promptly, mitigating the impact of the breach and reducing recovery time. Your organization can effectively contain the breach, preventing further data exposure. Additionally, having a plan in place demonstrates your commitment to data security, enhancing customer trust and loyalty. Finally, a well-prepared response plan can help streamline communication with external parties, such as regulators and affected individuals, which is crucial for compliance and reputation management.
By acknowledging the importance of having a data breach response plan and understanding its benefits, you can proactively protect your organization’s sensitive information and ensure its resilience in the face of potential cyber threats.

This image is property of images.pexels.com.
## III. Developing a Data Breach Response Plan
Building an effective data breach response plan is crucial for organizations of all sizes to effectively respond to and mitigate the impact of data breaches. By developing a well-structured plan, you can ensure that your response is timely, efficient, and minimizes the potential damage. This section will outline the key steps involved in developing a comprehensive data breach response plan.
A. Establishing a Cross-functional Response Team
To effectively handle a data breach, it is essential to assemble a cross-functional response team consisting of key stakeholders from various departments such as IT, legal, communications, and human resources. This team will be responsible for coordinating and executing the response plan, ensuring a cohesive and well-coordinated effort.
B. Conducting a Risk Assessment
A thorough risk assessment is vital to understand potential vulnerabilities, identify critical assets, and prioritize response efforts. By evaluating potential risks, you can develop appropriate strategies for prevention, detection, containment, and recovery.
C. Creating an Incident Response Policy
Developing an incident response policy ensures that everyone within the organization understands their roles and responsibilities during a data breach. It outlines the necessary protocols, guidelines, and steps to follow when responding to an incident.
D. Designating Incident Response Roles and Responsibilities
Identifying and assigning specific incident response roles and responsibilities is crucial for effective coordination and decision-making. This includes designating incident response team leaders, communication coordinators, legal representatives, and technical experts.
E. Building Communication Channels
Establishing clear communication channels internally and externally is vital for effective incident response. This includes defining who should be notified, when and how, ensuring rapid and accurate information dissemination to key stakeholders, including employees, customers, partners, and regulators.
F. Implementing Data Breach Detection Systems
Deploying advanced detection systems and monitoring tools can help identify and respond to a data breach more effectively. Utilize intrusion detection systems, security information and event management systems, and other relevant technologies to promptly detect and alert about any suspicious activities.
G. Developing an Escalation Process
Creating an escalation process ensures that any significant incidents are promptly escalated to the appropriate management level or external authorities as required. Establish clear criteria for escalating the incident based on its severity and potential impact.
H. Safeguarding and Securing Essential Data and Systems
Implement robust security measures to protect essential data and systems. This includes encryption, access controls, regular backups, and monitoring mechanisms. By safeguarding the critical assets, you minimize the risk of a data breach and ensure a more effective response.
I. Ensuring Incident Response Training and Awareness
Regularly train your employees on the incident response plan, including their roles, responsibilities, and how to identify and report potential security incidents promptly. Creating a culture of awareness and readiness enables a swift and effective response to any potential breach.
J. Regular Testing and Updating of the Plan
Periodically test and update your data breach response plan to ensure its effectiveness and relevance. Conducting mock drills and tabletop exercises helps identify any gaps or areas for improvement, allowing you to refine your plan and enhance your organization’s readiness.
Developing an effective data breach response plan requires a proactive and collaborative approach involving key stakeholders from various departments. By following these steps, you can establish a comprehensive and robust plan that enables your organization to respond efficiently and effectively to any data breach incidents. Remember, the key is to be prepared and proactive rather than reactive when it comes to data breaches.
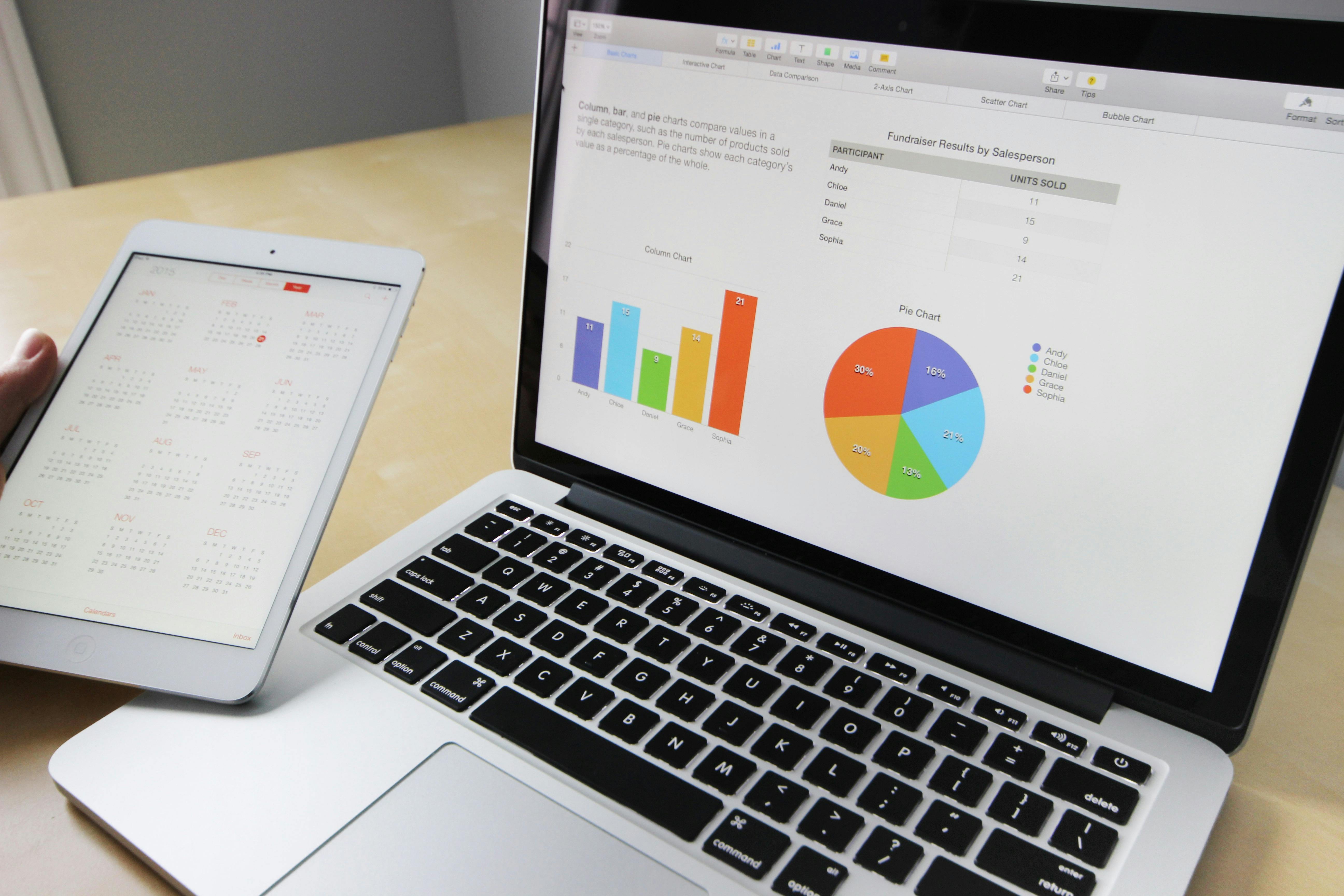
This image is property of images.pexels.com.
## Key Components of a Data Breach Response Plan
To effectively respond to a data breach, it is crucial to have a well-developed data breach response plan in place. Such a plan ensures that your organization is prepared and equipped to handle any potential security incidents and minimize the impact on your business. The key components of a comprehensive data breach response plan are as follows:
A. Incident Identification and Reporting
This section of the plan focuses on promptly identifying any potential data breaches and establishing clear reporting mechanisms. It includes guidelines for recognizing the signs of a breach, such as unusual network activity or unauthorized access attempts. Proper incident reporting protocols are essential, ensuring that all team members understand their role and responsibilities in reporting incidents to the appropriate authorities.
B. Containment and Mitigation
Once a breach is identified, the immediate goal is to contain the incident and mitigate any further damage. This component outlines the steps to be taken to isolate affected systems, disable compromised accounts, and prevent the breach from spreading. It also emphasizes the importance of implementing temporary security measures to limit unauthorized access.
C. Investigation and Root Cause Analysis
Following containment, the plan moves into the investigation phase. This involves conducting a thorough analysis of the breach to determine its root cause, the extent of the damage, and any vulnerabilities that may have contributed to the incident. It includes techniques such as log analysis, forensic examination, and interviewing relevant personnel to gather crucial information for resolving the breach and preventing future occurrences.
D. Notification and Communication
Transparent and timely communication throughout a data breach is essential to mitigate reputational damage and maintain customer trust. This section outlines the procedure for notifying affected individuals, regulatory bodies, and stakeholders. It emphasizes the need for providing clear and concise communication, including information on the breach, the potential impact on individuals, and steps they can take to protect themselves.
E. Remediation and Recovery
Once the breach is resolved, the focus shifts to remediation and recovery. This component encompasses the actions necessary to restore affected systems, strengthen security measures, and prevent future breaches. It includes plans for implementing security patches, upgrading systems, conducting employee training, and reviewing and updating security policies and procedures.
F. Post-Incident Review and Lessons Learned
The final component of the plan involves conducting a post-incident review to analyze the effectiveness of the response and identify areas for improvement. This includes evaluating the incident response process, providing feedback to team members, and updating the data breach response plan based on lessons learned. Regular reviews and updates ensure that the plan remains robust and up-to-date, enhancing your organization’s ability to handle future breaches effectively.
By integrating these key components into your data breach response plan, you can establish a comprehensive and effective framework for responding to security incidents, safeguarding your organization’s data, and minimizing potential damages.

This image is property of images.pexels.com.
## V. Preparing for a Data Breach
In order to effectively respond to a data breach, it is crucial to have a well-prepared and comprehensive plan in place. This section will provide you with valuable insights on how to prepare for a potential data breach and minimize its impact.
A. Documenting and Inventorying Sensitive Data
The first step in developing a solid data breach response plan is to document and inventory all the sensitive data your organization collects and stores. This includes personally identifiable information (PII), financial data, and any other confidential or proprietary information. By thoroughly understanding what data you have, where it is stored, and who has access to it, you can better assess the potential impact of a breach and take appropriate measures to mitigate the risks.
B. Implementing Security Controls and Best Practices
To prevent data breaches from occurring, it is essential to implement robust security controls and follow best practices. This includes regularly updating and patching your systems, using strong and unique passwords, encrypting sensitive data, and regularly monitoring and auditing your network for any signs of unauthorized access or suspicious activities. By proactively fortifying your defenses, you can significantly reduce the chances of a breach happening in the first place.
C. Creating Data Breach Response Templates
Having predefined data breach response templates can greatly expedite your response efforts and ensure consistency in handling incidents. These templates should outline step-by-step procedures for identifying, containing, and remediating data breaches, as well as notifying affected individuals and relevant authorities. By having these templates readily available, you can respond to breaches swiftly and efficiently, minimizing the potential harm caused.
D. Establishing Relationships with External Partners and Service Providers
In the event of a data breach, it is crucial to have established relationships with external partners and service providers who can provide assistance and expertise. This includes legal counsel, cybersecurity firms, public relations experts, and insurance providers. By establishing these relationships beforehand, you can ensure timely and effective response to a breach, minimizing its impact on your organization and its reputation.
By following these guidelines and investing in robust preparations, you can develop an effective data breach response plan that enables you to detect, respond to, and recover from a breach in a responsible and efficient manner. Remember, the key to effective breach response lies in proactive planning and preparedness.
VI. Legal and Regulatory Considerations
One crucial aspect of developing an effective data breach response plan is understanding the legal and regulatory considerations surrounding data protection. To ensure compliance with data protection laws, you need to be aware of the rules and regulations that govern your industry and the jurisdictions in which you operate.
A. Understanding Data Protection Laws
Data protection laws vary across countries and regions, and it is essential to familiarize yourself with the specific regulations that apply to your business. Understanding these laws will enable you to assess the potential impact of a data breach and ensure that your response plan aligns with legal requirements.
B. Compliance with Data Breach Notification Requirements
Many jurisdictions have specific data breach notification requirements that must be followed in the event of a breach. These requirements typically include notifying affected individuals, regulatory authorities, and, in some cases, the media. Your response plan should outline the steps you will take to comply with these notification requirements promptly and effectively.
C. Engaging Legal Counsel
Engaging legal counsel is crucial in developing and executing your data breach response plan. Legal professionals can provide guidance on compliance, breach notification obligations, and potential legal liabilities. Having legal counsel involved from the outset will help ensure that your response plan is legally sound and that you are prepared to navigate any legal challenges that may arise.
D. Addressing Liability and Reputational Risks
A data breach can have significant financial and reputational consequences for your organization. It is essential to address liability and reputational risks in your response plan. This includes considering potential legal liabilities, such as lawsuits or regulatory fines, and implementing measures to protect your organization’s reputation and rebuild trust with affected individuals and stakeholders.
Understanding data protection laws, compliance with notification requirements, engaging legal counsel, and addressing liability and reputational risks are critical elements of an effective data breach response plan. By carefully considering these legal and regulatory considerations, you can ensure that your plan is comprehensive, compliant, and able to mitigate potential damages resulting from a data breach.
VII. The Role of Public Relations
Data breaches can have severe consequences for businesses, damaging their reputation and eroding customer trust. That’s why developing an effective data breach response plan is crucial. Public relations plays a vital role in such a plan, as it focuses on managing communication, minimizing the negative impact, and rebuilding trust with stakeholders.
A. Developing a Communications Strategy
A well-thought-out communications strategy is essential during a data breach. This involves creating a clear and concise message for various audiences, including customers, employees, partners, and regulators. You should develop key talking points, frequently asked questions, and use appropriate channels such as websites, social media, press releases, and call centers to effectively communicate important information.
B. Managing Media and Public Relations
During a breach, media attention can intensify, and managing the narrative becomes critical. You must designate a spokesperson to handle media inquiries promptly and effectively. Developing relationships with trusted media contacts can also help ensure accurate reporting. Providing accurate and timely updates, while being transparent about the situation, demonstrates your commitment to resolving the issue.
C. Rebuilding Trust and Handling Reputation Damage
Rebuilding trust in the aftermath of a data breach is a significant challenge. It requires a proactive approach that includes taking responsibility, offering solutions, and providing ongoing support to affected individuals. Your response should be focused on addressing customer concerns, offering identity theft protection services, and implementing measures to prevent future breaches. Communicating these efforts effectively will help mitigate reputation damage and rebuild trust among stakeholders.
Public relations plays a crucial role in developing an effective data breach response plan. By developing a communications strategy, managing media and public relations, and actively working to rebuild trust, businesses can navigate the aftermath of a breach with transparency and integrity.
VIII. Incident Response in the Digital Age
In today’s rapidly evolving digital landscape, it is essential for organizations to have a well-defined data breach response plan in place. This section explores various challenges and considerations that need to be taken into account when developing such a plan, as well as emerging trends and technologies that can enhance incident response capabilities.
A. Challenges and Considerations in the Modern Landscape
With the increasing frequency and complexity of cyber attacks, organizations face numerous challenges in effectively responding to data breaches. These include the need for rapid detection and containment, compliance with data protection regulations, and managing potential reputational damage. It is crucial to consider both technical and legal aspects when developing a response plan to ensure a comprehensive approach.
B. Emerging Trends and Technologies in Incident Response
The field of incident response is constantly evolving, with new trends and technologies emerging to assist organizations in dealing with data breaches. From automated incident response systems to threat intelligence platforms, these advancements enable quicker identification and containment of breaches, reducing the potential impact on the organization.
C. Harnessing Artificial Intelligence for Early Detection and Response
Artificial intelligence (AI) holds great promise in augmenting incident response capabilities. By leveraging machine learning algorithms, organizations can detect abnormal patterns and behaviors, allowing for early identification and swift response to potential breaches. AI also facilitates the automation of certain response tasks, freeing up valuable time and resources.
D. Addressing Cloud Security Concerns
As more organizations migrate their data and infrastructure to the cloud, addressing cloud security concerns becomes increasingly important in incident response planning. Factors such as data segregation, access controls, and encryption must be carefully considered to ensure data breaches are effectively managed in a cloud environment.
Ultimately, developing an effective data breach response plan requires a comprehensive understanding of the challenges and considerations in the modern landscape. Adopting emerging trends and technologies, such as harnessing AI and addressing cloud security concerns, can significantly enhance an organization’s ability to respond to data breaches promptly and effectively.
IX. Case Studies: Effective Data Breach Response
It is crucial to examine case studies of successful data breach response in order to develop an effective data breach response plan. By learning from real-life examples, you can gain valuable insights and lessons that will help you mitigate the impact of a potential breach on your organization.
A. Examples of Successful Incident Response
In this section, we will explore various instances where organizations successfully handled data breaches. These case studies highlight the key elements of an effective response plan, including timely detection of the breach, swift containment of the incident, communication with affected parties, and implementation of remediation measures. By analyzing these examples, you can identify best practices and apply them to your own response plan.
B. Lessons Learned from High-Profile Data Breaches
Examining high-profile data breaches not only sheds light on the devastating consequences of a data breach but also provides valuable lessons that can be learned from such incidents. By studying the mistakes made by organizations that experienced major breaches, you can understand the importance of proactive security measures and robust incident response strategies. This knowledge will help you better prepare and protect your data from potential breaches, ultimately minimizing the impact on your organization and its stakeholders.
By studying these case studies and lessons learned, you will be equipped with the knowledge and insights necessary to develop an effective data breach response plan. Investing time and effort into this crucial aspect of cybersecurity will enable you to respond swiftly and mitigate potential damages in the event of a breach. Remember, preparation is key to safeguarding your organization’s sensitive data and maintaining the trust of your customers and stakeholders.
Conclusion
Recap of the Importance of a Data Breach Response Plan
In today’s digital landscape, where data breaches have become increasingly common, it is vital for organizations to have a well-developed and effective data breach response plan. A data breach can result in severe financial and reputational damage, as well as legal and regulatory consequences.
Having a robust plan in place allows you to respond quickly and effectively to minimize the impact of a breach. It enables you to identify and contain the breach, notify affected individuals, and provide necessary support to mitigate any potential harm.
Steps to Implement an Effective Plan
Developing an effective data breach response plan involves several key steps. First, you need to assemble a dedicated incident response team consisting of professionals from different departments, such as IT, legal, communications, and human resources. This team should be responsible for creating and implementing the plan.
Next, conduct a thorough risk assessment to identify potential vulnerabilities and determine the necessary security measures to prevent breaches. This assessment should cover both technical aspects, such as firewalls and encryption, as well as organizational processes and employee training.
Once the plan is developed, it must be regularly tested, updated, and communicated to all relevant stakeholders within the organization. Training sessions and mock drills can ensure that everyone is aware of their roles and responsibilities in the event of a breach.
By following these steps and developing a comprehensive data breach response plan, you can safeguard your organization against the damaging consequences of a breach. Remember, preparedness is key in the fight against data breaches.

3 replies on “Data Breach Response Plan: Developing An Effective Data Breach Response Plan.”
[…] Data breach notification laws are a crucial aspect of cybersecurity regulations and data protection laws. These laws require organizations to notify individuals and authorities in the event of a data breach that compromises their personal information. […]
[…] data is stored in multiple locations. This ensures that even if one server fails or experiences a data breach, your information remains safe and […]
[…] precautions, data breaches may still occur. Be prepared by creating a comprehensive data breach response plan. This plan should include steps to contain the breach, notify affected customers, and […]